Integrate new firewalls into Panorama via CLI
September 15, 2017 Leave a comment
I recently switched jobs and I am excited to announce that I am working with Palo Alto firewalls again. I am not gonna lie, I am beyond excited seeing PANs again. There is just something about them that I like.
As much as I love the UI it is somewhat annoying to integrate a new Palo Alto in Panorama. The reason is that PANs come with a standard configuration which has a standard security policy, virtual-wires and security zones. Now when you want to add it to Panorama this will cause some problems because it interferes with the config you want to push from Panorama. And after all, you want to get rid of any configuration that you may not use. Now you must click through the WebUI and delete the standard configuration in the correct order to avoid dependency errors. Just to hit “commit” and get another error thrown at you.
Hence I referred to the CLI and looked up all commands to wipe and stage a new device for our environment. I basically wanted to have a copy/paste deployment procedure to save time and drive standardization. The Palo Alto CLI is very capable and I was pleasantly surprised about the awesome readability of the commands. Below you will find my staging scripts for the local device and Panorama.
Example deployment “script” for PA firewall
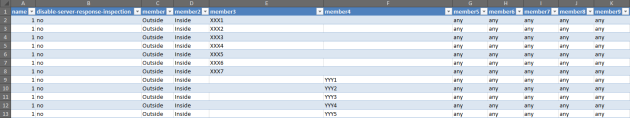
For easier deployment, I build a small excel file that will build all the commands to
- wipe the standard configuration
- setup the management interface
- set the panorama server
- setup the interfaces so that interface configurations can be pushed via Panorama templates
- setup HA
- update the license
- check and install dynamic updates
- check and install software updates
Basic setup of 3 interfaces as layer 3 and port 7 and 8 for HA1/2:
# Setup MGMT interface
set deviceconfig system ip-address <MGMT-IP> netmask <netmask in X.X.X.X> default-gateway <default-gw-IP> dns-setting servers primary <primary-DNS>
# Setup Panorama server
set deviceconfig system panorama-server <IP/DNS of your Panorama Server>
# Delete standard config
delete network virtual-wire default-vwire
delete rulebase security rules rule1
delete zone trust
delete zone untrust
delete network interface ethernet ethernet1/1
delete network interface ethernet ethernet1/2
delete network interface ethernet ethernet1/3
delete network interface ethernet ethernet1/4
delete network interface ethernet ethernet1/5
delete network interface ethernet ethernet1/6
delete network interface ethernet ethernet1/7
delete network interface ethernet ethernet1/8
# Assign minimum configuration to network interfaces to be able to push Panorama templates
set network interface ethernet ethernet1/7 ha
set network interface ethernet ethernet1/7 comment HA1
set network interface ethernet ethernet1/8 ha
set network interface ethernet ethernet1/8 comment HA2
set network interface ethernet ethernet1/1 layer3 ip X.X.X.X/XX
set network interface ethernet ethernet1/1 comment <interface1comment>
set network interface ethernet ethernet1/2 layer3 ip X.X.X.X/XX
set network interface ethernet ethernet1/2 comment <interface2comment>
set network interface ethernet ethernet1/3 layer3 ip X.X.X.X/XX
set network interface ethernet ethernet1/3 comment <interface3comment>
set network virtual-router default interface ethernet1/1
set network virtual-router default interface ethernet1/2
set network virtual-router default interface ethernet1/3
# Setup hostname
set deviceconfig system hostname <hostname>
# Setup HA
set deviceconfig high-availability enabled yes
set deviceconfig high-availability group 1
set deviceconfig high-availability group 1 peer-ip X.X.X.X peer-ip-backup X.X.X.X
set deviceconfig high-availability interface ha1 port ethernet1/7
set deviceconfig high-availability interface ha1 ip-address X.X.X.X netmask X.X.X.X
set deviceconfig high-availability interface ha1-backup port management
set deviceconfig high-availability interface ha2 port ethernet1/8
set deviceconfig high-availability interface ha2 ip-address X.X.X.X netmask X.X.X.X
commit
# Update license on local firewall
request license fetch
# Check for App updates and install latest
request content upgrade check
request content upgrade download latest
request content upgrade install sync-to-peer yes version latest
# Check for AV updates and install latest
request anti-virus upgrade check
request anti-virus upgrade download latest
request anti-virus upgrade install sync-to-peer yes version latest
Example deployment “script” for Panorama
This will do the following on the Panorama Server:
- Add serial number to Managed Devices
- Clone a template
- Create a template stack
- Add templates to template stack
- Add new device to template stack
- Add new device to log-collector
set mgt-config devices <serial-nr>
# copy a template
copy template <template1> to <template2>
# Create template stack, add templates and add new device
set template-stack <template-stack>
set template-stack <template-stack> templates <template1>
set template-stack <template-stack> templates <template2>
set template-stack <template-stack> devices <serial-nr>
# Add new device to log collector
set log-collector-group default logfwd-setting devices <serial-nr> collectors <serial-nr-of-collector>
Hit commit and push the template to device (don’t forget to force values on first push).
No rocket science here, it is all very simple CLI commands, but maybe I will save someone some time to look up all these commands and it will for sure save you some time clicking through the WebUI and hitting dependency errors.
I used the commands above together with an excel file which will automatically put in IPs and serial numbers collected from a form. All commands are tested with version PAN-OS 8.0.4